Research
Understanding distributed systems infrastructure
Since the creation of bitcoin and subsequent innovations in blockchain technologies, we have seen a resurgence of interest in distributed systems and peer-to-peer networks. Although blockchain networks are a relatively new paradigm, the foundations on which they are based date back to the 1960s with the emergence of the first computer networks.
To understand blockchain technology, it is useful to have a basic understanding of the field of computing from which it originated, namely distributed computing.
This article sets out to classify blockchain networks within the broader field of study known as distributed systems, and differentiates blockchain technologies from digital ledger technologies.
Distributed computing
The history of distributed computing is closely linked to that of the Internet and the primitive networks that preceded it. When computer networks began to emerge in the 1960s, the idea that they could act in unison to achieve common goals became obvious. One of the earliest examples of a distributed system was ARPANET, the forerunner of the modern Internet, and later ARPANET e-mail, which went online in the early 1970s.
Distributed systems are made up of several independent, interconnected computing units (nodes), each with its own memory. The nodes communicate with each other by transmitting messages using a common protocol. These protocols are sometimes referred to as “gossip networks”.
The nodes of distributed systems work in coordination to achieve a common goal. In many cases, the objective is to solve large computational problems that would otherwise be inaccessible to a single computer. However, they have qualities other than the system’s superior computing capabilities.
- Fault tolerance: the system can continue to operate if certain nodes fail, up to a certain threshold.
- Partial knowledge: each node only has access to part of the data processed by the system as a whole.
Examples of distributed systems include telecommunications networks, such as cellular networks; network applications, such as the World Wide Web and Bitcoin; industrial systems, such as air traffic control systems; and parallel computing networks, such as distributed video rendering and the human genome project.
Major distributed ledger
A distributed ledger is a system of replicated, shared and synchronised digital data, distributed geographically across several sites, countries or institutions. A peer-to-peer network of nodes (participants) takes part in a consensus protocol that ensures data replication across all nodes.
Often referred to as “distributed ledger technology” (DLT), this term can be confusing. It is not necessarily a single technology, but rather several concepts and technologies that can be deployed as a system. There are a number of vendors and open-source projects offering DLT software specialising in a wide range of applications.
Trust assumptions
Distributed ledgers operate on a contradictory trust model in which other nodes cannot be trusted. Participants in a distributed ledger network assume that other participants are untrustworthy, but they cooperate to present a single source of truth to external users. There is no central authority or administrator in a distributed ledger network.
This contrasts with distributed databases, which have existed in production applications for several decades. Although they share many similarities with distributed ledgers, there is one aspect that generally sets them apart: trust between participants. This is because the participants in a distributed database operate on the assumption that the other nodes are trustworthy. This is why distributed databases are generally deployed and controlled by a single administrator.
Properties of distributed ledgers
Large digital books have three main properties.
Immutable
Compared with traditional databases, which operate on the CRUD model (create, read, update, delete), distributed ledgers are appendices only. This means that users can only read and add records – records cannot be modified or deleted.
Shared
The ledger is accessed and maintained by a group of participants who have a common interest in accurate data.
Distributed
Data is duplicated and replicated on participants’ nodes, making it resistant to breakdowns and censorship.
These properties make distributed ledgers highly resilient and, as an artefact, unforgeable.
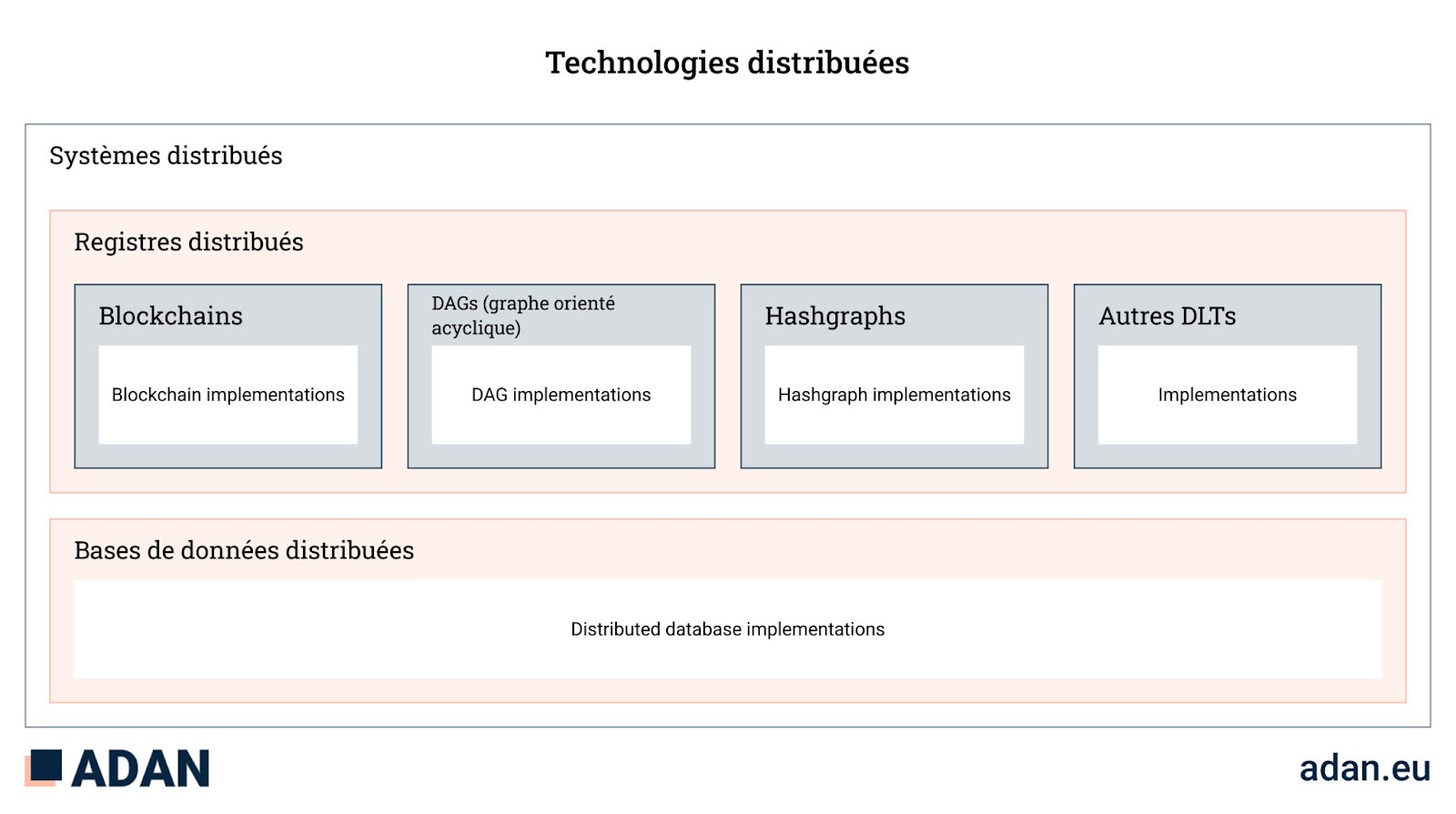
Examples of distributed ledger applications
- Hash graph
- Acyclic oriented graph
- Blockchain
A blockchain is a type of distributed ledger in which data is grouped together in a growing list of records called blocks that refer to each other using cryptography. Each block contains a cryptographic hash of the previous block, a timestamp and raw data.
Blockchains inherit the distributed ledger concept, in that their data is a) replicated, b) shared between participants, and c) synchronised between participants. Blockchains generally offer the possibility of generating a consensus enabling participants to establish a single source of truth about data integrity. In theory, a blockchain protocol can have only one participant and thus lose its distributed characteristic. In practice, however, this configuration is of little use, if only in the initial phases of the life of a blockchain network where the aim is to add participants later on.
Blockchain networks are well suited to applications where stakeholders require a) time-stamped data, b) a record of its mutation over time, and c) the preservation and assurance of the integrity of the state of that data. In practice, the most common applications are in finance.
Blockchain technologies and financial applications
Financial markets require data integrity and symmetry of information between participants. Today, these guarantees are provided by regulatory oversight of market participants, where the government’s mandate ensures a level playing field for participants and the smooth functioning of markets. In traditional market structures, participants rely on infrastructure, information and services provided by private entities to create a reliable market environment.
Blockchain-based financial applications shift some forms of trust from authorities and regulated entities to cryptoeconomic protocols. These applications exist on peer-to-peer networks made up of anonymous or semi-anonymous stakeholders. These networks are generally referred to as “public” blockchain networks, in that they operate on the public internet and allow anyone to interact with the protocol.
Examples of displaced confidence
- Solvency of the compound money market: solvency can be verified and ensured by the blockchain network without the need for an authority to maintain the solvency of the system.
- Transaction settlement: transactions are settled and verified by the blockchain network without the need for an authority or regulated intermediary to check their validity.
Examples where trust is not transferred
- Preventing insider trading: the role of the authorities remains the same, because the blockchain network cannot guarantee a level playing field against insider trading by default.
Examples where the authorities have a potentially more important role to play
- Systemic risk in blockchain protocols, where the failure of one protocol can have cascading effects on other protocols, leading to a collapse in market activity.
Crypto-economic protocols reduce dependence on intermediaries by aligning economic incentives. In the case of blockchain networks, these incentives motivate participants to provide the time-stamped, reliable and symmetrical data needed for markets to function. Indeed, blockchain technology creates a new base layer for the emergence of various forms of markets and the flourishing of interesting financial instruments.
Understanding the “open-closed” spectrum of blockchain
Since the emergence of blockchain networks that allow transactions to be executed programmatically (e.g. Ethereum), so-called “public” and “private” blockchains have been the subject of debate. They may also be colloquially referred to as “permissionless” and “permissioned” networks, respectively.
The distinction between private and public blockchain networks is based solely on their implementation – the underlying technology stack has no way of understanding its own configuration. In fact, it is possible to configure a blockchain network so that access is more, or less, open.
It is more appropriate to talk about open or closed systems operating on blockchain networks. As we shall see, there are nuances that can make a blockchain network more or less open. The term “open” is more appropriate, just as a door can be opened to a multitude of degrees, blockchain networks can be configured in any number of ways that create a gradient across the open-closed spectrum. This contrasts with the public and private terminology often used, which leaves no room for light between these two extremes.
Note: Open access should not be confused with the concept of free software. Although the overwhelming majority of blockchain protocols are indeed open-source, this refers to a different idea.
The term “open” refers to the ability of any legal entity to take advantage of blockchain to conduct its business. An open blockchain network is an autonomous platform on which economic activity can take place, meaning that anyone can participate in the market by validating transactions, developing applications that provide value, use services or carry out transactions. In effect, open blockchain networks are economic platforms where the rules of the market are applied by the protocol.
Closed blockchain networks generally serve the interests of a group of participants who wish to collaborate or do business around a use case or niche application. They are custom-built and access is limited to a small number of interested players.
Although fully closed, or ‘permissioned’, blockchain networks seemed to cater for a subset of applications in the early development phase of the technology, advances in scalability, privacy and security allow most applications to exist on open networks. This change is analogous to the way in which corporate intranets, common in the 90s and early 80s, have moved to the cloud over the last decade. Similarly, as technologies advance and gain acceptance, open blockchain networks will take over most applications. Furthermore, as with the Internet infrastructure, it is possible to create ‘closed’ applications on open blockchain networks.
Note: “private” or “authorised” networks should not be confused with the distributed ledger technologies described above. Indeed, a blockchain is a form of DLT. However, a DLT is not a blockchain. There may be a DLT that does not embody all the properties of a blockchain, whatever its configuration.
In summary, the idea of open blockchain networks and closed networks are not strictly opposed to each other. There are nuances and gradients of authorised access, which makes it difficult to classify each of these concepts into well-defined categories.
Roles of network participants
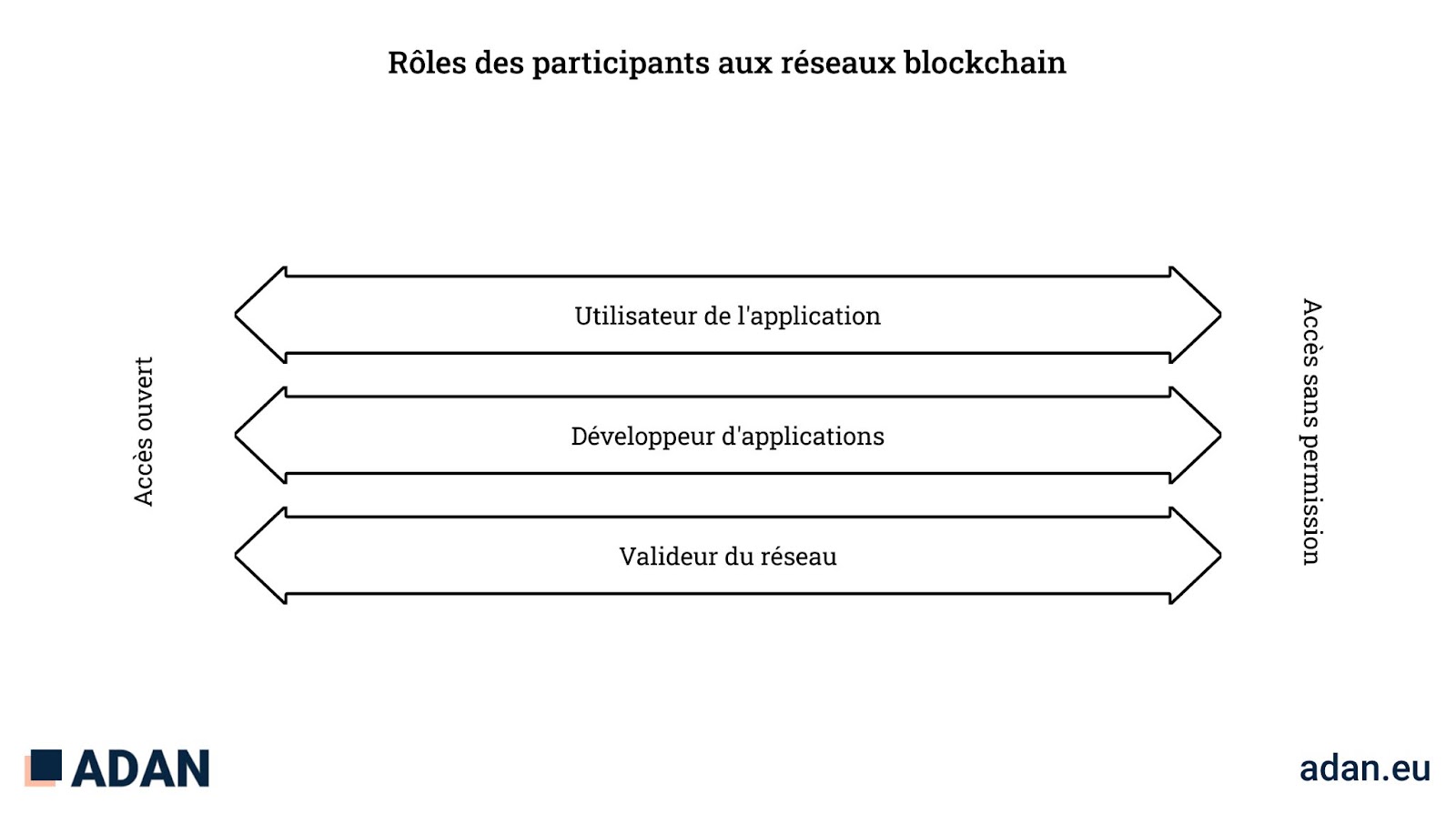
When interacting with a blockchain network, a participant can play three main roles:
- the user of the application, such as sending and receiving transactions, and interacting with applications ;
- applications developer, such as the development and deployment of smart contracts, and ;
- network validator, such as block approval by participating in consensus (e.g. mining, staking).
These roles may overlap because participants may take on different functions (for example, block validation activities require transactions to be sent and received).
Roles of participants in the blockchain network
While, as a general rule, blockchain networks allow completely open access to these three roles (so-called “public” blockchain networks) or restrict access to authorised entities (so-called “private” blockchain networks), there are practical and theoretical examples where the public/private classification is not so clear-cut.
The backbone of the Internet is built on open protocols and standards (e.g. TCP/IP, HTTP, SMTP), and open networks operated by private companies. Similarly, open blockchain networks can support production applications built by private companies with universal access.
While blockchain networks generally allow completely open access to these three functions or limit access to private players, there are practical and theoretical examples where the open/closed classification is not clear.
To illustrate certain cases where the open vs. closed classification is not so clear, we can contrast three different systems currently being implemented, all potentially useful for issuing securities on a blockchain network:
- The ERC20 token standard. It allows an issuer to issue securities on the Ethereum core network, a public blockchain network with open validation. ERC20 tokens can be transferred between any pairs of users. No identifying information is required before transactions can be submitted.
- The ST20 token standard. This allows an issuer to issue securities on the Ethereum mainnet, a public blockchain network with open validation. ST20 token transfers require the sending and receiving accounts to have their identities registered with the issuer. The issuer can also create policies for approving or rejecting ST20 token transfers. Although the underlying infrastructure is “open”, the ST20 standard that underpins it limits open access.
- A closed Ethereum network. This allows the issuer to create a blockchain network specifically designed for issuing securities. The underlying infrastructure of the blockchain is closed and validation is reserved for identified entities.
Conclusion
In conclusion, the emergence of blockchain technologies has attracted enormous attention and research in the areas of peer-to-peer systems, cryptography, game theory and the areas where they overlap. Over the past decade, exciting new distributed systems have emerged that serve practical applications in crypto-finance.
In this context, it is important to understand these technologies, their unique characteristics and their applications. As blockchain networks and applications develop and become regulated, it is in the interest of policymakers to be precise so that private companies can continue to innovate and consumers are protected.